Quick summary ↬
In this tutorial we install Nginx, ModSecurity and then connect them together. To give some context ModSecurity is a open source firewall which could be configured with any HTTP server. In this tutorial we install it along with the Nginx web server.
1. Virtual machine setup and upgrade
Buy a VM from any bare metal provider who gives root access. I bought it from Vultr. Linode, DigitalOcean or any VPS provider works.
1
|
sudo apt update && sudo apt upgrade
|
2. Install Nginx from Ubuntu package manager
Check the nginx version using the command nginx -v. In this tutorial we installed nginx/1.14.0 (Ubuntu) version. But any stable version of nginx could be connected to ModSecurity WAF using the ModSecurity Connector.
3. Libraries required for the ModSecurity installation
Install the below libraries which may take upto 5 minutes to finish installation.
1
|
sudo apt-get install bison build-essential ca-certificates curl dh-autoreconf doxygen flex gawk git iputils-ping libcurl4-gnutls-dev libexpat1-dev libgeoip-dev liblmdb-dev libpcre3-dev libpcre++-dev libssl-dev libtool libxml2 libxml2-dev libyajl-dev locales lua5.3-dev pkg-config wget zlib1g-dev zlibc
|
4. Test whether Nginx is running
Just type the IP address of the machine in the browser. It should display something as shown in the below image. If it is not showing the nginx page then firewall is blocking the port so just need to unblock it using the below command:
1
2
3
4
|
ufw allow 80/tcp
ufw allow 80/tcp
ufw allow 443/tcp
ufw allow 443/udp
|
5. Download the ModSecurity and compile it manually
This helps us to connect it as a shared library with Nginx and it work at ease. Cloning the ModSecurity inside the /opt/ folder.
1
2
3
4
5
6
7
8
9
10
11
|
cd /opt/
git clone https://github.com/SpiderLabs/ModSecurity
cd ModSecurity
sudo git submodule init
sudo git submodule update
sudo ./build.sh
sudo make
sudo ./build.sh
sudo ./configure
sudo make
sudo make install
|
The above commands will download the main ModSecurity repo, update the submodules, build them, make and configure before installing.
6. Download the ModSecurity connector and install it
Go back to the folder /opt/ and clone the ModSecurity connector.
1
|
cd /opt && sudo git clone --depth 1 https://github.com/SpiderLabs/ModSecurity-nginx.git
|
7. Download the Nginx version installed and re-install manually with the ModSecurity configuration in place
1
2
3
4
5
|
cd /opt
wget http://nginx.org/download/nginx-1.14.0.tar.gz
tar -xzvf nginx-1.14.0.tar.gz
cd nginx-1.14.0/
nginx -V
|
The above command will display the configuration of the existing Nginx installation. The output looks as shown below:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
|
--with-cc-opt='-g -O2 -fdebug-prefix-map=/build/nginx-YlUNvj/nginx-1.14.0=. -fstack-protector-strong
-Wformat -Werror=format-security -fPIC -Wdate-time -D_FORTIFY_SOURCE=2'
--with-ld-opt='-Wl,-Bsymbolic-functions -Wl,-z,relro -Wl,-z,now -fPIC'
--prefix=/usr/share/nginx
--conf-path=/etc/nginx/nginx.conf
--http-log-path=/var/log/nginx/access.log
--error-log-path=/var/log/nginx/error.log
--lock-path=/var/lock/nginx.lock
--pid-path=/run/nginx.pid
--modules-path=/usr/lib/nginx/modules
--http-client-body-temp-path=/var/lib/nginx/body
--http-fastcgi-temp-path=/var/lib/nginx/fastcgi
--http-proxy-temp-path=/var/lib/nginx/proxy
--http-scgi-temp-path=/var/lib/nginx/scgi
--http-uwsgi-temp-path=/var/lib/nginx/uwsgi
--with-debug
--with-pcre-jit
--with-http_ssl_module
--with-http_stub_status_module
--with-http_realip_module
--with-http_auth_request_module
--with-http_v2_module
--with-http_dav_module
--with-http_slice_module
--with-threads
--with-http_addition_module
--with-http_geoip_module=dynamic
--with-http_gunzip_module
--with-http_gzip_static_module
--with-http_image_filter_module=dynamic
--with-http_sub_module
--with-http_xslt_module=dynamic
--with-stream=dynamic
--with-stream_ssl_module
--with-mail=dynamic
--with-mail_ssl_module
|
We already downloaded the ModSecurity connector. Now we need to connect it with the nginx and re-install the nginx again using the same configs as shown above.
1
2
3
4
5
|
sudo apt install libxslt-dev -y
sudo apt install libgd-dev -y
cd /opt/nginx-1.14.0/
nginx -V
./configure --with-cc-opt='-g -O2 -fdebug-prefix-map=/build/nginx-YlUNvj/nginx-1.14.0=. -fstack-protector-strong -Wformat -Werror=format-security -fPIC -Wdate-time -D_FORTIFY_SOURCE=2' --with-ld-opt='-Wl,-Bsymbolic-functions -Wl,-z,relro -Wl,-z,now -fPIC' --prefix=/usr/share/nginx --conf-path=/etc/nginx/nginx.conf --http-log-path=/var/log/nginx/access.log --error-log-path=/var/log/nginx/error.log --lock-path=/var/lock/nginx.lock --pid-path=/run/nginx.pid --modules-path=/usr/lib/nginx/modules --http-client-body-temp-path=/var/lib/nginx/body --http-fastcgi-temp-path=/var/lib/nginx/fastcgi --http-proxy-temp-path=/var/lib/nginx/proxy --http-scgi-temp-path=/var/lib/nginx/scgi --http-uwsgi-temp-path=/var/lib/nginx/uwsgi --with-debug --with-pcre-jit --with-http_ssl_module --with-http_stub_status_module --with-http_realip_module --with-http_auth_request_module --with-http_v2_module --with-http_dav_module --with-http_slice_module --with-threads --with-http_addition_module --with-http_geoip_module=dynamic --with-http_gunzip_module --with-http_gzip_static_module --with-http_image_filter_module=dynamic --with-http_sub_module --with-http_xslt_module=dynamic --with-stream=dynamic --with-stream_ssl_module --with-mail=dynamic --with-mail_ssl_module --add-dynamic-module=../ModSecurity-nginx
|
Notice that I added –add-dynamic-module=../ModSecurity-nginx at the end.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
|
checking for OS
+ Linux 4.15.0-202-generic x86_64
checking for C compiler ... found
+ using GNU C compiler
+ gcc version: 7.5.0 (Ubuntu 7.5.0-3ubuntu1~18.04)
checking for gcc -pipe switch ... found
checking for --with-ld-opt="-Wl,-Bsymbolic-functions -Wl,-z,relro -Wl,-z,now -fPIC" ... found
checking for -Wl,-E switch ... found
checking for gcc builtin atomic operations ... found
checking for C99 variadic macros ... found
checking for gcc variadic macros ... found
checking for gcc builtin 64 bit byteswap ... found
checking for unistd.h ... found
checking for inttypes.h ... found
checking for limits.h ... found
checking for sys/filio.h ... not found
checking for sys/param.h ... found
checking for sys/mount.h ... found
checking for sys/statvfs.h ... found
checking for crypt.h ... found
checking for Linux specific features
checking for epoll ... found
checking for EPOLLRDHUP ... found
checking for EPOLLEXCLUSIVE ... found
checking for O_PATH ... found
checking for sendfile() ... found
checking for sendfile64() ... found
checking for sys/prctl.h ... found
checking for prctl(PR_SET_DUMPABLE) ... found
checking for prctl(PR_SET_KEEPCAPS) ... found
checking for capabilities ... found
checking for crypt_r() ... found
checking for sys/vfs.h ... found
checking for nobody group ... not found
checking for nogroup group ... found
checking for poll() ... found
checking for /dev/poll ... not found
checking for kqueue ... not found
checking for crypt() ... not found
checking for crypt() in libcrypt ... found
checking for F_READAHEAD ... not found
checking for posix_fadvise() ... found
checking for O_DIRECT ... found
checking for F_NOCACHE ... not found
checking for directio() ... not found
checking for statfs() ... found
checking for statvfs() ... found
checking for dlopen() ... not found
checking for dlopen() in libdl ... found
checking for sched_yield() ... found
checking for sched_setaffinity() ... found
checking for SO_SETFIB ... not found
checking for SO_REUSEPORT ... found
checking for SO_ACCEPTFILTER ... not found
checking for SO_BINDANY ... not found
checking for IP_TRANSPARENT ... found
checking for IP_BINDANY ... not found
checking for IP_BIND_ADDRESS_NO_PORT ... found
checking for IP_RECVDSTADDR ... not found
checking for IP_SENDSRCADDR ... not found
checking for IP_PKTINFO ... found
checking for IPV6_RECVPKTINFO ... found
checking for TCP_DEFER_ACCEPT ... found
checking for TCP_KEEPIDLE ... found
checking for TCP_FASTOPEN ... found
checking for TCP_INFO ... found
checking for accept4() ... found
checking for eventfd() ... found
checking for int size ... 4 bytes
checking for long size ... 8 bytes
checking for long long size ... 8 bytes
checking for void * size ... 8 bytes
checking for uint32_t ... found
checking for uint64_t ... found
checking for sig_atomic_t ... found
checking for sig_atomic_t size ... 4 bytes
checking for socklen_t ... found
checking for in_addr_t ... found
checking for in_port_t ... found
checking for rlim_t ... found
checking for uintptr_t ... uintptr_t found
checking for system byte ordering ... little endian
checking for size_t size ... 8 bytes
checking for off_t size ... 8 bytes
checking for time_t size ... 8 bytes
checking for AF_INET6 ... found
checking for setproctitle() ... not found
checking for pread() ... found
checking for pwrite() ... found
checking for pwritev() ... found
checking for sys_nerr ... found
checking for localtime_r() ... found
checking for clock_gettime(CLOCK_MONOTONIC) ... found
checking for posix_memalign() ... found
checking for memalign() ... found
checking for mmap(MAP_ANON|MAP_SHARED) ... found
checking for mmap("/dev/zero", MAP_SHARED) ... found
checking for System V shared memory ... found
checking for POSIX semaphores ... not found
checking for POSIX semaphores in libpthread ... found
checking for struct msghdr.msg_control ... found
checking for ioctl(FIONBIO) ... found
checking for struct tm.tm_gmtoff ... found
checking for struct dirent.d_namlen ... not found
checking for struct dirent.d_type ... found
checking for sysconf(_SC_NPROCESSORS_ONLN) ... found
checking for sysconf(_SC_LEVEL1_DCACHE_LINESIZE) ... found
checking for openat(), fstatat() ... found
checking for getaddrinfo() ... found
configuring additional dynamic modules
adding module in ../ModSecurity-nginx
checking for ModSecurity library ... not found
checking for ModSecurity library in /usr/local/modsecurity ... found
+ ngx_http_modsecurity_module was configured
checking for PCRE library ... found
checking for PCRE JIT support ... found
checking for OpenSSL library ... found
checking for zlib library ... found
checking for libxslt ... found
checking for libexslt ... found
checking for GD library ... found
checking for GD WebP support ... found
checking for GeoIP library ... found
checking for GeoIP IPv6 support ... found
creating objs/Makefile
Configuration summary
+ using threads
+ using system PCRE library
+ using system OpenSSL library
+ using system zlib library
nginx path prefix: "/usr/share/nginx"
nginx binary file: "/usr/share/nginx/sbin/nginx"
nginx modules path: "/usr/lib/nginx/modules"
nginx configuration prefix: "/etc/nginx"
nginx configuration file: "/etc/nginx/nginx.conf"
nginx pid file: "/run/nginx.pid"
nginx error log file: "/var/log/nginx/error.log"
nginx http access log file: "/var/log/nginx/access.log"
nginx http client request body temporary files: "/var/lib/nginx/body"
nginx http proxy temporary files: "/var/lib/nginx/proxy"
nginx http fastcgi temporary files: "/var/lib/nginx/fastcgi"
nginx http uwsgi temporary files: "/var/lib/nginx/uwsgi"
nginx http scgi temporary files: "/var/lib/nginx/scgi"
|
Once the configure is successful and resulted in the the logs as shown above the next step is to integrate the shared lib
ngx_http_modsecurity_module.so to the
/etc/nginx/module

Look for ngx_http_modesecurity_module.so as shown in the above image.
1
2
3
4
|
make modules
ls objs
mkdir /etc/nginx/module
cp objs/ngx_http_modsecurity_module.so /etc/nginx/module
|
Edit the nginx.conf using your favourite editor. I am using VIM editor.
1
|
vi /etc/nginx/nginx.conf
|
Add the below line in the nginx.conf file to load the modsecurity module into the nginx HTTP server.
load_module /etc/nginx/module/ngx_http_modsecurity_module.so.
8. OWASP Core rule set and Modsecurity configuration
We clone the core rule set from OWASP and add it to the ModSecurity configuration.
1
2
3
4
5
6
7
8
9
10
11
12
13
|
cd /opt/
git clone https://github.com/coreruleset/coreruleset modsecurity-crs
cd modsecurity-crs/
mv crs-setup.conf.example crs-setup.conf
mv rules/REQUEST-900-EXCLUSION-RULES-BEFORE-CRS.conf rules/REQUEST-900-EXCLUSION-RULES-BEFORE-CRS.conf
mv rules/REQUEST-900-EXCLUSION-RULES-BEFORE-CRS.conf.example rules/REQUEST-900-EXCLUSION-RULES-BEFORE-CRS.conf
cd ..
mv modsecurity-crs /usr/local/
mkdir -p /etc/nginx/modsec
cp /opt/ModSecurity/unicode.mapping /etc/nginx/modsec
cd ModSecurity
mv modsecurity.conf-recommended modsecurity.conf
cp modsecurity.conf /etc/nginx/modsec/
|
Edit the file /etc/nginx/modsec/modsecurity.conf and change the SecRuleEngine from detection only to just On.
1
2
3
4
5
6
7
|
# -- Rule engine initialization ----------------------------------------------
# Enable ModSecurity, attaching it to every transaction. Use detection
# only to start with, because that minimises the chances of post-installation
# disruption.
#
SecRuleEngine On
|
Main.conf needs to be edited as shown below:
1
2
3
|
ls -alps
cd ..
ls -alps
|
Edit the vi /etc/nginx/modsec/main.conf and add the below three lines in it.
1
2
3
|
Include /etc/nginx/modsec/modsecurity.conf
Include /usr/local/modsecurity-crs/crs-setup.conf
Include /usr/local/modsecurity-crs/rules/*.conf
|
Find all the mod security modules as shown below in the folder /etc/nginx/
Now, add the modsecurity in the nginx.
Edit the file /etc/nginx/sites-available/default and add the below lines to turn on ModSecurity in Nginx.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
|
# Default server configuration
#
server {
listen 80 default_server;
listen [::]:80 default_server;
# SSL configuration
#
# listen 443 ssl default_server;
# listen [::]:443 ssl default_server;
#
# Note: You should disable gzip for SSL traffic.
# See: https://bugs.debian.org/773332
#
# Read up on ssl_ciphers to ensure a secure configuration.
# See: https://bugs.debian.org/765782
#
# Self signed certs generated by the ssl-cert package
# Don't use them in a production server!
#
# include snippets/snakeoil.conf;
root /var/www/html;
modsecurity on;
modsecurity_rules_file /etc/nginx/modsec/main.conf;
|
Notice the modsecurity on; and modsecurity_rules_file /etc/nginx/modsec/main.conf; in the default server configuration. This is how we configure modsecurity in the Nginx and add OWASP rules in it. Now it’s time to test.
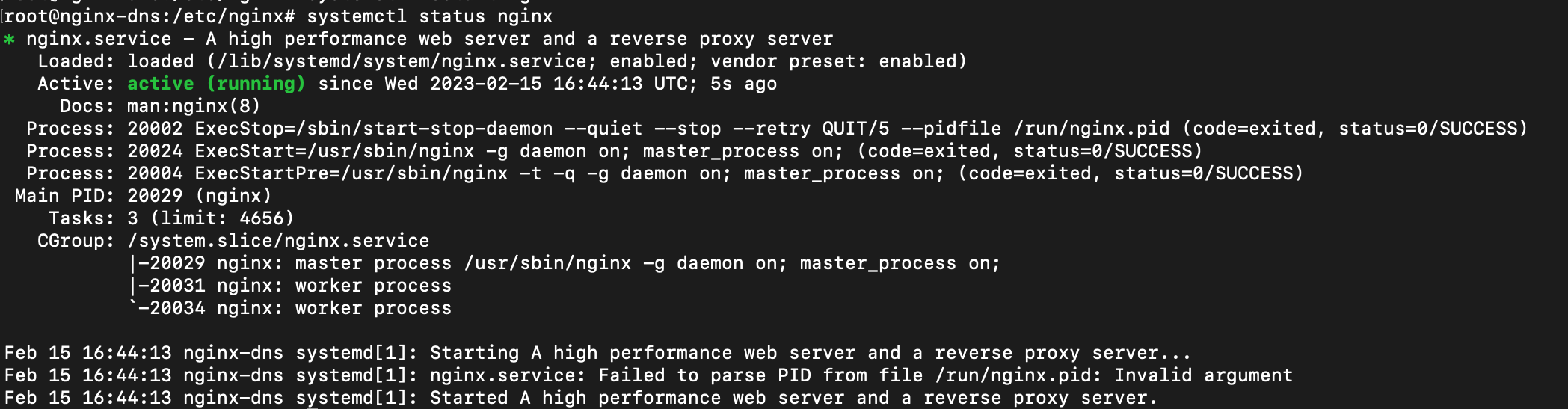
Restart the Nginx HTTP server using the systemctl command. systemctl restart nginx.
Check the status as shown in the below image:
Let’s attack the firewall and test whether ModSecurity takes any action against our attack.
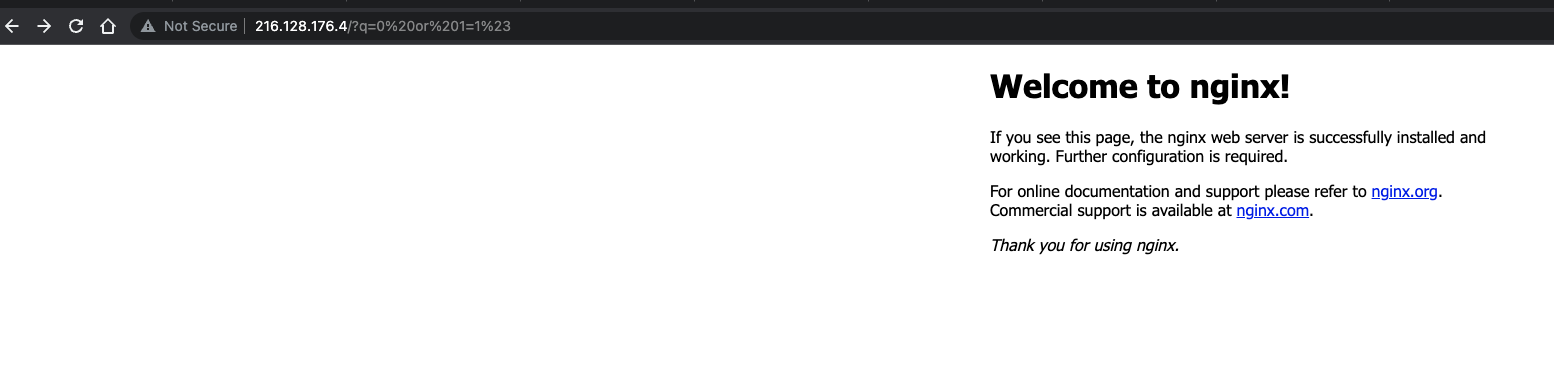
When the modsecurity off; in the file /etc/nginx/modsec/main.conf then the firewall does not work and allow SQL injection payload in the URL as shown in the below image:
When the modsecurity on; in the file /etc/nginx/modsec/main.conf then the firewall blocks the SQL injection as shown in the below image:
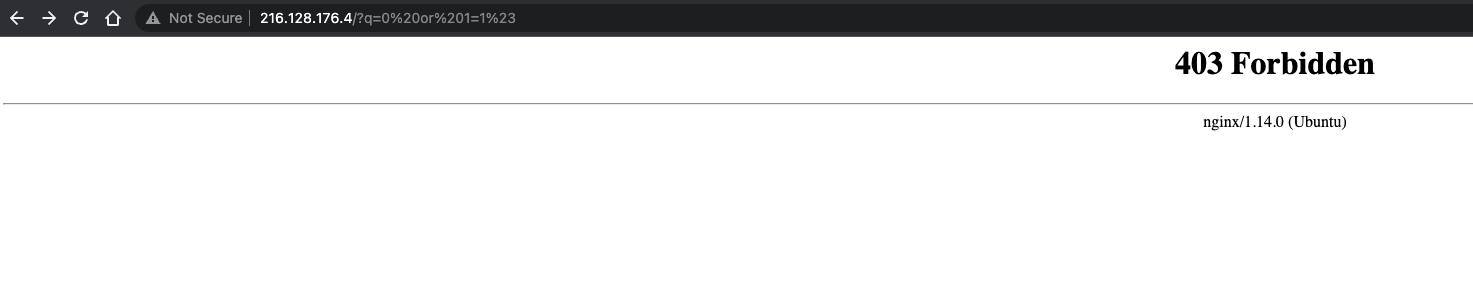
Evrytime you turn on and turn off the modsecurity module make sure to restart the Nginx Web server. Happy learning.
9. Conclusion
We setup the Nginx from system package manager, extracted the configs, installed Modsecurity, installed the core rule set from OWASP and then installed the Nginx from the source and applied all the default configs along with the modsecurity configs using the modsecurtity connector.
We also tested the Modsecurity + Nginx installation by doing an SQL injection attack on the web server and showing that Modsecurity rules protect the Nginx server if kept turned on.






